- This is the official OpenVPN Connect client software for Windows workstation platforms developed and maintained by OpenVPN Inc. This is the recommended client program for the OpenVPN Access Server to enable VPN for Windows. The latest version of OpenVPN for Windows is available on our website.
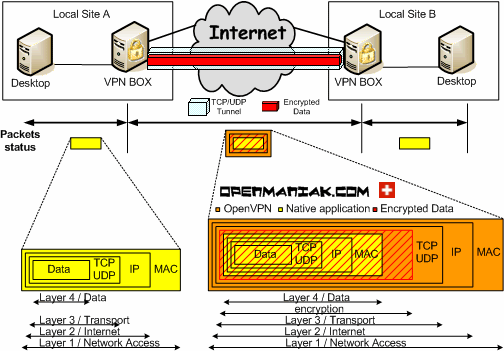
- A secure sockets layer VPN (SSL VPN) enables individual users to access an organization's network, client-server applications, and internal network utilities and directories without the need for.
- Connecting to SSL VPN Service for Mass remote Access Use the following steps to connect from your home PC to your desktop. USE Internet Explorer (IE) to access the URL (this will not work on any other browser). If you don't have IE listed as a browser to choose, please do the following. Click on the magnifying glass and type internet explorer.
- Setup SSL VPN Road Warrior¶. Road Warriors are remote users who need secure access to the companies infrastructure. OPNsense uses OpenVPN for its SSL VPN Road Warrior setup and offers OTP (One Time Password) integration with standard tokens and Googles Authenticator.
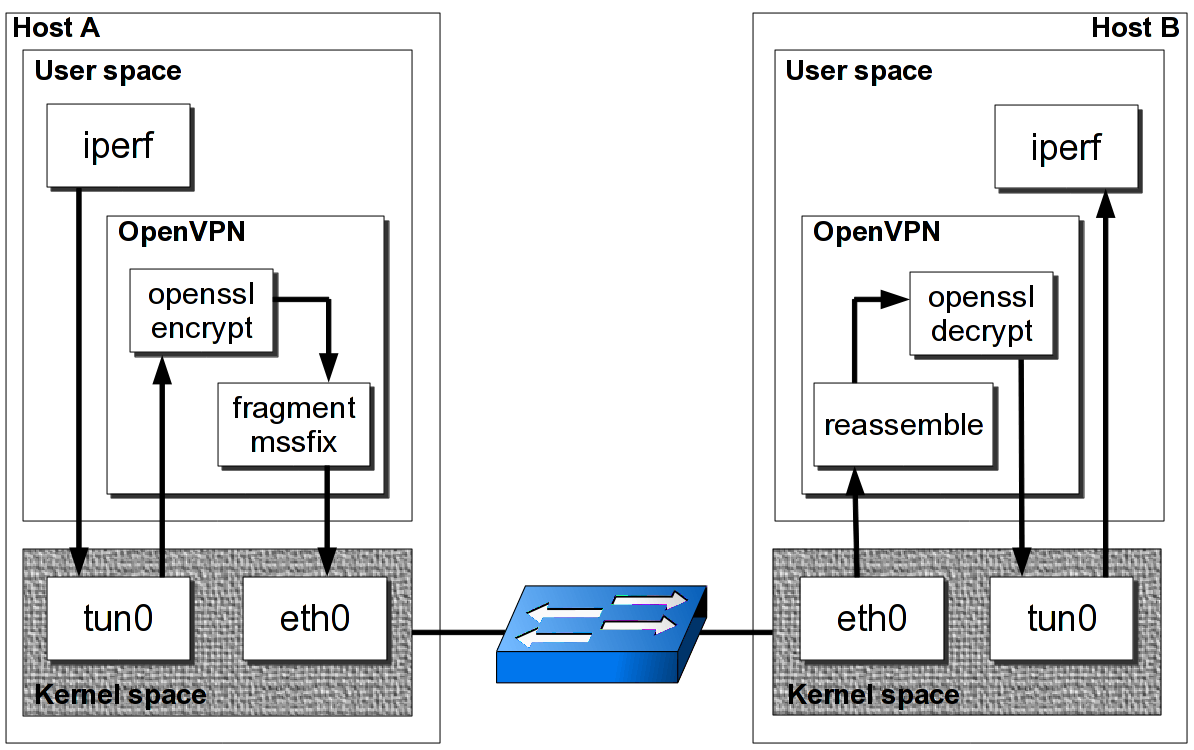
Viscosity is a first class VPN client, providing everything you need to establish fast and secure OpenVPN connections on both macOS and Windows. Viscosity caters to both users new to VPNs and experts alike, providing secure and reliable VPN connections.
The purpose of this post is to describe the steps to setup and configure an OpenSSL Certificate Authority (CA) on an Ubuntu server. The CA will be used for VPN authentication for Windows Client authenticating against a Cisco Router. It is assumed that the Ubuntu server is already installed and configured. Important to note, time accuracy is important when using certificates, so ensure the Ubuntu servers' time is correct.
The following software/hardware was utilised:-
- Ubuntu Server 16.04
- Cisco Router 1921 15.4
- Windows 7 Professional with AnyConnect VPN client
Create CA directory structure
A folder structure must be created on the server, it is important to remember the file/folder names are case sensitive AND the location of the files created later in this guide are referenced in the openssl configuration file openssl.cnf.
Create the CA folder
sudo su
mkdir /root/CA
Create the sub-folder structure underneath the root CA folder
cd /root/CA
mkdir certs crl newcerts private requests
- Create an index file keeps track of the signed certificates touch index.txt
- Create a Serial file will define the unique serial, starting at 1000 echo ‘1000' > serial
Configure OpenSSL
When modifying the configuration file be careful as the file and folder names are case sensitive.
- Modify the openssl.cnf file, enter the command sudo vi /usr/lib/ssl/openssl.cnf
- Press i to start writing.
Modify the folder name, change from /demoCA and set the default_days (length of the certificate) to 1825 (5 years)
[ CA_default ]
dir = /root/CA
default_days = 1825
Under policy_match section, set countryName, storeOrProvinceName and organsationName to optional
[ policy_match ]
countryName = optional
stateOrProvinceName = optional
organizationName = optional
- Save the configuration by pressing ESC, then type :wq! To write and quit
Create Root Certificate and Private Key
- Generate the CA Root Private Key (do not change file name, unless modified in openssl.cnf) using the command openssl genrsa -aes256 -out private/cakey.pem 4096
Enter a Pass Phrase when prompted
- Create Root Certificate using Private Key (do not change file name, unless modified in openssl.cnf) using the command openssl req -new -x509 -key /root/CA/private/cakey.pem -out cacert.pem -days 7300 -set_serial 0
Enter a Pass Phrase when prompted
Enter Country Name, State, Locality, Organisation Name, Organisation Unit, Common Name and Email address when prompted
The Root Certificate called cacert.pem should be created in /root/CA and the Private Key cakey.pem should be located in /root/CA/private folder.
Windows does not recognise PEM format, so make a copy of the cacert.pem file to cacert.crt for use later on, use the command cp /root/CA/cacert.pem cacert.crt
Create a Client Certificate
In this scenario we will create a certificate for a Windows computer to use for VPN authentication. A Private Key and Certificate Signing Request (CSR) will be created and the certificate signed by the CA. The signed certificate, private key and the Root Certificate will then be bundled in a PKCS12 file
- Change directory to cd /root/CA/requests
- Generate Private Key using the command openssl genrsa -aes256 -out clientkey.pem 2048
Enter a Pass Phrase when prompted
- Create CSR using the command openssl req -new -key clientkey.pem -out client.csr
- Sign CSR using the command openssl ca -in client.csr -out client.crt
- Create PKCS12 File using the command openssl pkcs12 -export -out client.p12 -inkey clientkey.pem -in client.crt -certfile /root/CA/cacert.crt
Enter the Certificate Pass Phrase when prompted (the same pass phrase used in the previous steps)
Enter a new unique export password for the PKCS12 file
- Verify the PKCS12 file to confirm it contains the client certificate, root certificate and client private key using the command openssl pkcs12 -info -in client.p12
Enter a Import Password when prompted
The client certificate should be listed first; you can confirm this by checking CN of the subject
Immediately below the end of the client certificate, the Root Certificate should be displayed next. You can confirm this by checking the CN of the subject.
Enter PEM pass phrase when prompted (this is the pass phrase of the private key for the client certificate, as specified when creating the private key).
Import PKCS12 on Windows Computer
- Copy the PKCS12 file client.p12 to the Window computer
- Double click the client.p12 file
- When prompted click Next
- When prompted click Next
- Enter the export password specified when creating the PKCS12 file previously
- When prompted click Next
- When prompted click Finish
- When prompted click Yes to install the certificate
- When prompted click Ok
- Open an MMC add a snap-in for Certificates > select My user account
- Expand Personal > Certificates you should see the client certificate
- Double click the certificate and confirm You have a private key that corresponds to this certificate message is displayed. This confirms the bundled PKCS12 file of the certificate and private key worked.
- Click Certification Path to confirm the Root Certificate is part of the trusted certification path
- Click Ok to finish
- Navigate to Trusted Root Certificates > Certificates
- Locate the Root Certificate
With the Root Certificate present in the Trusted Root Certificate Store this confirms the bundled root certificate was also correctly imported from the PKCS12 file. With the client certificate/private key pair and the root certificate this should be enough for the client to user digital signatures for VPN authentication.
Certificate Enrolment on Cisco Router
On the Cisco router an RSA key pair and trustpoint must be configured, the router will then generate a CSR which will be signed by the CA and subsequently imported to the router.
Unlike the CSR created for the Windows computer the CSR will not be generated on the CA but locally on the router (as will the associated private key). Therefore the signed certificate, private key nor the CA Root Certificate do not need to be bundled into a PKCS12 file.
- Remove existing RSA Key Pair, enter the command crypto key zeroize rsa
- Create new RSA Key Pair, enter the command crypto key generate rsa modulus 2048 label VPN_KEY
- Create a new Trustpoint as below
crypto pki trustpoint VPN_TP
enrollment terminal
serial-number none
fqdn CSR2.lab.net
ip-address none
subject-name cn=CSR2.lab.net,o=LAB,ou=IT Services,st=London,c=GB
revocation-check none
rsakeypair VPN_KEY
exit
Modify the fqdn and subject-name accordingly; they must match the FQDN DNS name used by the VPN client in order not to receive any certificate upon connection to the VPN.
- Authenticate the Trustpoint to import the CA Root Certificate, enter the command crypto pki authenticate VPN_TP
When prompted copy the contents of the cacert.crt file located on the CA into the terminal window of the Cisco Router.
- To create CSR for the router, enter the command crypto pki enroll VPN_TP
- Press y to display the certificate request in the terminal window
- Copy the contents of the CSR to a notepad file
- Add a new first line to the CSR notepad file, enter —–BEGIN CERTIFICATE REQUEST—–
- Add a new last line to the CSR notepad file, enter —–END CERTIFICATE REQUEST—–
On the Linux Server
- On the Linux CA CLI, navigate to /root/CA/requests
- Create a new file for the CSR, enter the command vi router2.csr
- Press i to start to edit the file
- Paste the contents of the CSR file into the file (note the format of the new first and last lines)
- Once the data has been pasted into the file, press ESC and then type :wq! to save and exit
- To complete the signing request, enter the command openssl ca -in router2.csr -out router2.crt
- Enter the pass phrase of the Root Certificate when prompted
- Press y to sign the certificate and commit when prompted
- Type cat router2.crt to display the output of the certificate
- Copy the contents of the certificate from the line starting ——BEGIN CERTIFICATE —– and finishing —–END CERTIFICATE —–
On the Router
- Enter the command crypto pki import VPN_TP certificate
- When prompted paste the contents of the signed certificate, then type quit
The router should import the certificate successfully and should now be ready for use in authenticating VPNs.
On the cisco router type show crypto pki certificates, this will display the certificate and the CA certificate and the associated trustpoint.
The previous post on how to configure a FlexVPN Remote Access VPN explains the steps involved to configure the VPN on the router.
Road Warriors are remote users who need secure access to the companies infrastructure.OPNsense uses OpenVPN for its SSL VPN Road Warrior setup and offers OTP (One Time Password)integration with standard tokens and Googles Authenticator.
Tip
Did you know that OPNsense offers two-factor authentication throughout the entiresystem? See for more information: Two-factor authentication
The main advantages of using SSL VPN for Road Warriors instead of IPsec are:
Easy setup on almost all mobile clients using OPNsense's Client Configuration Export.
Fine grained access control by using multiple servers or Client Specific Overrides.
No issues with NAT without NAT-T
With this how-to we'll show you how to configure OPNsense's SSL VPN for road warriorsand give you configuration examples for:
Two Factor Authentication (2FA)
Multi Factor Authentication ( Client Certificate + Password + OTP )
Client configuration on Windows, macOS, iOS and Android
Note
For the sample we will use a private IP for our WAN connection.This requires us to disable the default block rule on wan to allow private traffic.To do so, go to Interfaces ‣ [WAN] and uncheck 'Block private networks'.(Dont forget to save and apply)
Sample Setup¶
For the sample configuration we configure OPNsense
Company Network with Remote Client
Company Network¶
Hostname | fw1 |
WAN IP | 172.18.0.129 |
LAN IP | 192.168.1.1/24 |
LAN DHCP Range | 192.168.1.100-192.168.1.200 |
SSL VPN Clients | 10.10.0.0/24 |
Step 0 - Preparation¶
For our example we will use two factor authentication (2FA) and multi factor authentication.So before we start with the SSL VPN configuration we will need an TOTP server anda valid signing certificate authority.
For completeness of this how-to we will also prepare a user.
Configure TOTP server¶
To configure a Time based One Time Password server go to System ‣ Access ‣ Serversand click Add in the top right corner of the form.
Tip
You can also use the quick-search to jump right into the the Access Serverconfiguration. Try it by typing Ac… and see for yourself:
Now first change the Type to Local + Timebased One time PasswordEnter a Descriptive name such as TOTP VPN Access Server
For our example we leave everything else default as we will be using Google's Authenticatorand the defaults are correct for that.

When using other tokens you may need to change the Token length.

Openssl Vpn Client Mac
Click Save to add the new server.
Under policy_match section, set countryName, storeOrProvinceName and organsationName to optional
[ policy_match ]
countryName = optional
stateOrProvinceName = optional
organizationName = optional
- Save the configuration by pressing ESC, then type :wq! To write and quit
Create Root Certificate and Private Key
- Generate the CA Root Private Key (do not change file name, unless modified in openssl.cnf) using the command openssl genrsa -aes256 -out private/cakey.pem 4096
Enter a Pass Phrase when prompted
- Create Root Certificate using Private Key (do not change file name, unless modified in openssl.cnf) using the command openssl req -new -x509 -key /root/CA/private/cakey.pem -out cacert.pem -days 7300 -set_serial 0
Enter a Pass Phrase when prompted
Enter Country Name, State, Locality, Organisation Name, Organisation Unit, Common Name and Email address when prompted
The Root Certificate called cacert.pem should be created in /root/CA and the Private Key cakey.pem should be located in /root/CA/private folder.
Windows does not recognise PEM format, so make a copy of the cacert.pem file to cacert.crt for use later on, use the command cp /root/CA/cacert.pem cacert.crt
Create a Client Certificate
In this scenario we will create a certificate for a Windows computer to use for VPN authentication. A Private Key and Certificate Signing Request (CSR) will be created and the certificate signed by the CA. The signed certificate, private key and the Root Certificate will then be bundled in a PKCS12 file
- Change directory to cd /root/CA/requests
- Generate Private Key using the command openssl genrsa -aes256 -out clientkey.pem 2048
Enter a Pass Phrase when prompted
- Create CSR using the command openssl req -new -key clientkey.pem -out client.csr
- Sign CSR using the command openssl ca -in client.csr -out client.crt
- Create PKCS12 File using the command openssl pkcs12 -export -out client.p12 -inkey clientkey.pem -in client.crt -certfile /root/CA/cacert.crt
Enter the Certificate Pass Phrase when prompted (the same pass phrase used in the previous steps)
Enter a new unique export password for the PKCS12 file
- Verify the PKCS12 file to confirm it contains the client certificate, root certificate and client private key using the command openssl pkcs12 -info -in client.p12
Enter a Import Password when prompted
The client certificate should be listed first; you can confirm this by checking CN of the subject
Immediately below the end of the client certificate, the Root Certificate should be displayed next. You can confirm this by checking the CN of the subject.
Enter PEM pass phrase when prompted (this is the pass phrase of the private key for the client certificate, as specified when creating the private key).
Import PKCS12 on Windows Computer
- Copy the PKCS12 file client.p12 to the Window computer
- Double click the client.p12 file
- When prompted click Next
- When prompted click Next
- Enter the export password specified when creating the PKCS12 file previously
- When prompted click Next
- When prompted click Finish
- When prompted click Yes to install the certificate
- When prompted click Ok
- Open an MMC add a snap-in for Certificates > select My user account
- Expand Personal > Certificates you should see the client certificate
- Double click the certificate and confirm You have a private key that corresponds to this certificate message is displayed. This confirms the bundled PKCS12 file of the certificate and private key worked.
- Click Certification Path to confirm the Root Certificate is part of the trusted certification path
- Click Ok to finish
- Navigate to Trusted Root Certificates > Certificates
- Locate the Root Certificate
With the Root Certificate present in the Trusted Root Certificate Store this confirms the bundled root certificate was also correctly imported from the PKCS12 file. With the client certificate/private key pair and the root certificate this should be enough for the client to user digital signatures for VPN authentication.
Certificate Enrolment on Cisco Router
On the Cisco router an RSA key pair and trustpoint must be configured, the router will then generate a CSR which will be signed by the CA and subsequently imported to the router.
Unlike the CSR created for the Windows computer the CSR will not be generated on the CA but locally on the router (as will the associated private key). Therefore the signed certificate, private key nor the CA Root Certificate do not need to be bundled into a PKCS12 file.
- Remove existing RSA Key Pair, enter the command crypto key zeroize rsa
- Create new RSA Key Pair, enter the command crypto key generate rsa modulus 2048 label VPN_KEY
- Create a new Trustpoint as below
crypto pki trustpoint VPN_TP
enrollment terminal
serial-number none
fqdn CSR2.lab.net
ip-address none
subject-name cn=CSR2.lab.net,o=LAB,ou=IT Services,st=London,c=GB
revocation-check none
rsakeypair VPN_KEY
exit
Modify the fqdn and subject-name accordingly; they must match the FQDN DNS name used by the VPN client in order not to receive any certificate upon connection to the VPN.
- Authenticate the Trustpoint to import the CA Root Certificate, enter the command crypto pki authenticate VPN_TP
When prompted copy the contents of the cacert.crt file located on the CA into the terminal window of the Cisco Router.
- To create CSR for the router, enter the command crypto pki enroll VPN_TP
- Press y to display the certificate request in the terminal window
- Copy the contents of the CSR to a notepad file
- Add a new first line to the CSR notepad file, enter —–BEGIN CERTIFICATE REQUEST—–
- Add a new last line to the CSR notepad file, enter —–END CERTIFICATE REQUEST—–
On the Linux Server
- On the Linux CA CLI, navigate to /root/CA/requests
- Create a new file for the CSR, enter the command vi router2.csr
- Press i to start to edit the file
- Paste the contents of the CSR file into the file (note the format of the new first and last lines)
- Once the data has been pasted into the file, press ESC and then type :wq! to save and exit
- To complete the signing request, enter the command openssl ca -in router2.csr -out router2.crt
- Enter the pass phrase of the Root Certificate when prompted
- Press y to sign the certificate and commit when prompted
- Type cat router2.crt to display the output of the certificate
- Copy the contents of the certificate from the line starting ——BEGIN CERTIFICATE —– and finishing —–END CERTIFICATE —–
On the Router
- Enter the command crypto pki import VPN_TP certificate
- When prompted paste the contents of the signed certificate, then type quit
The router should import the certificate successfully and should now be ready for use in authenticating VPNs.
On the cisco router type show crypto pki certificates, this will display the certificate and the CA certificate and the associated trustpoint.
The previous post on how to configure a FlexVPN Remote Access VPN explains the steps involved to configure the VPN on the router.
Road Warriors are remote users who need secure access to the companies infrastructure.OPNsense uses OpenVPN for its SSL VPN Road Warrior setup and offers OTP (One Time Password)integration with standard tokens and Googles Authenticator.
Tip
Did you know that OPNsense offers two-factor authentication throughout the entiresystem? See for more information: Two-factor authentication
The main advantages of using SSL VPN for Road Warriors instead of IPsec are:
Easy setup on almost all mobile clients using OPNsense's Client Configuration Export.
Fine grained access control by using multiple servers or Client Specific Overrides.
No issues with NAT without NAT-T
With this how-to we'll show you how to configure OPNsense's SSL VPN for road warriorsand give you configuration examples for:
Two Factor Authentication (2FA)
Multi Factor Authentication ( Client Certificate + Password + OTP )
Client configuration on Windows, macOS, iOS and Android
Note
For the sample we will use a private IP for our WAN connection.This requires us to disable the default block rule on wan to allow private traffic.To do so, go to Interfaces ‣ [WAN] and uncheck 'Block private networks'.(Dont forget to save and apply)
Sample Setup¶
For the sample configuration we configure OPNsense
Company Network with Remote Client
Company Network¶
Hostname | fw1 |
WAN IP | 172.18.0.129 |
LAN IP | 192.168.1.1/24 |
LAN DHCP Range | 192.168.1.100-192.168.1.200 |
SSL VPN Clients | 10.10.0.0/24 |
Step 0 - Preparation¶
For our example we will use two factor authentication (2FA) and multi factor authentication.So before we start with the SSL VPN configuration we will need an TOTP server anda valid signing certificate authority.
For completeness of this how-to we will also prepare a user.
Configure TOTP server¶
To configure a Time based One Time Password server go to System ‣ Access ‣ Serversand click Add in the top right corner of the form.
Tip
You can also use the quick-search to jump right into the the Access Serverconfiguration. Try it by typing Ac… and see for yourself:
Now first change the Type to Local + Timebased One time PasswordEnter a Descriptive name such as TOTP VPN Access Server
For our example we leave everything else default as we will be using Google's Authenticatorand the defaults are correct for that.
When using other tokens you may need to change the Token length.
Openssl Vpn Client Mac
Click Save to add the new server.
Openssl Vpn
Add Certificate Authority¶
The VPN server needs a certificate authority to sign client or server certificates.
To setup a new certificate authority go to System ‣ Trust ‣ Authorities and clickAdd in the top right corner of the form.
For our example we will use the following setting:
Descriptive name | SSL VPN CA |
Method | Create an internal Certificate Authority |
Key length (bits) | 4096 |
Digest Algorithm | SHA512 |
Lifetime (days) | 365 |
Country Code | NL |
State or Province | ZH |
City | Merge fields in excel. Middelharnis |
Organization | OPNsense |
Email Address | spam@opnsense.org |
Common Name | internal-sslvpn-ca |
Click Save to add the new Certificate Authority.
Create a Server Certificate¶
After creating the Authority we will also need a certificate.To create a new certificate, go to System ‣ Trust ‣ Certificates and clickAdd in the upper right corner of the form.
Fill in the form with (leave the rest default):
Method | Create an internal Certificate |
Descriptive name | SSLVPN Server Certificate |
Certificate authority | SSL VPN CA |
Type | Server Certificate |
Key length (bits) | 4096 |
Digest Algorithm | SHA512 |
Lifetime (days) | 365 |
Country Code | NL |
State or Province | ZH |
City | Middelharnis |
Organization | OPNsense |
Email Address | spam@opnsense.org |
Common Name | SSLVPN Server Certificate |
Click Save to create the certificate.
Adding a User¶
To add a new user go to System ‣ Access ‣ Users and click Add in the topright corner.
Creating a user will be done in two steps, the first one is adding a basic userwith a username, password, TOTP seed and user certificate. The second step(after saving) will be to activate the generated OTP seed with a GoogleAuthenticator compatible app.
For the first step we enter:
Username | Donald |
Password (2x) | S3cr3tP@ssw0rd |
Full name | Donald Duck |
Certificate | Check 'Click to create a user certificate' |
OTP seed | Check 'Generate new secret' |
Click Save and you will be redirected to create the User Certificate.Fill in the Certificate form with the following for our example (leave anythingnot listed on its presented defaults):
Method | Create an internal Certificate |
Descriptive Name | Leave default (Donald) |
Certificate authority | SSL VPN CA |
Type | Client Certificate |
Key length | 4096 |
Digest Algorithm | SHA512 |
Click Save and you will be redirected to the User page.Now we will activate your newly created seed with your Google Authenticatorcompatible app. To do so click in the Click to unhide button in theOTP QR code row and you will get a QR code to scan with your smartphone.See also: Configure 2FA TOTP & Google Authenticator
Note
Always make sure to use the same Certificate authority as the certificate authority created earlier, asthis links the clients / users to the correct openvpn server.
Step 1 - Add SSL Server¶
Adding a new SSL VPN server is relatively simple. We'll start by adding one thatuses our two factor authentication. This setup offers a good protection and it iseasy to setup on the clients as each client can use the same configuration.
Go to VPN ‣ OpenVPN ‣ Servers and click Add in the top right cornerof the form.
For our example will use the following settings:
Note
The setting Hardware Crypto is not used for new systems equipped with AES-NI,when the aesni module is loaded it will be used automatically.
Description | My SSL VPN Server |
Server Mode | Remote Access (SSL/TLS + User Auth) |
Backend for authentication | TOTP VPN Access Server |
Protocol | UDP |
Device Mode | tun |
Interface Teams virtual meeting. Virtual events with Microsoft Teams Host secure, interactive webinars and events for 1,000 attendees and broadcasts for up to 10,000. Make meetings more personal and encourage teamwork when you virtually meet face-to-face. Meet in any situation, whether you're calling one-on-one, delivering a sales pitch, hosting a team training, or running a company-wide town hall. Teams provides the meeting organizer with many options when it comes to defining the roles and permissions for online meeting participants. You can choose to enable a meeting lobby, which lets the organizer define who can be admitted into the meeting and when. You can also designate who can present, mute attendees, start/stop recordings, and more. | WAN |
Local port | 1194 |
TLS Authentication | Leave both on enabled (checked) |
Peer Certificate Revocation List | N/A |
Server Certificate | SSLVPN Server Certificate (CA: SSL VPN CA) |
DH Parameters Length | 4096 bit |
Encryption algorithm | AES-256-CBC (256-bit key, 128-bit block) |
Auth Digest Algorithm | SHA512 (512-bit) |
Hardware Crypto | No Hardware Crypto Acceleration |
Certificate Depth | One (Client+Server) |
IPv4 Tunnel Network | 10.10.0.0/24 |
IPv6 Tunnel Network | Leave Empty |
Redirect Gateway | Leave Unchecked |
IPv4 Local Network/s | 192.168.1.0/24 |
IPv6 Local Network/s | Leave Empty |
IPv4 Remote Network/s | Leave Empty |
IPv6 Remote Network/s | Leave Empty |
Concurrent connections | Leave Empty |
Compression | Enabled with Adaptive Compression |
Type-of-Service | Leave Unchecked |
Duplicate Connections | Leave Unchecked |
Disable IPv6 | Checked |
Dynamic IP | Leave Unchecked |
Address Pool | Leave Checked |
Topology | Leave Unchecked |
DNS Default Domain | Leave Unchecked |
DNS Servers | Leave Unchecked |
Force DNS cache update | Leave Unchecked |
NTP Servers | Leave Unchecked |
NetBIOS Options | Leave Unchecked |
Client Management Port | Leave Unchecked |
Renegotiate time | 0 |
Note
Renegotiate time is used to renegotiate data channel key after nseconds (default=3600).When using a one time password, be advised thatyour connection will automatically drop because your password is notvalid anymore.Set to 0 to disable, remember to change your client whenchanged later.
Click Save to add the new server.
Tip
Use Strict User/CN Matching to force the usage of the same username as certificate CN, this preventspeople from logging in using other credentials than the certificate name supplied. (e.g. fred can't login as root)
Tip
The option Enforce local group can be used to constraint access to only users in a specific (set of) group(s)
Step 2 - Firewall Rules¶
To allow SSL VPN client connections, we should allow access to the OpenVPN serverport on the WAN interface. When using multiple servers we need to open up each port.
For our configuration we only use one server, accessible on UDP port 1194.
Next we also need to allow traffic from the VPN clients to our LAN interface.For our example we will allow client to access anything on our local area network,however you may decide just to allow traffic to one or more servers.
Step 3 - Export Client Configuration¶
Using the Remote Access Server dropdown you can select the server for which you want to download client files,when there are certificates connected (using the same authority) it will list all available client certificates andattached users.
macOS & Windows¶
For macOS & Windows users we recommend using Viscosity from Sparklabs (https://www.sparklabs.com/viscosity/).Viscosity is very easy to setup and use and works well on both platforms.
Go to VPN ‣ OpenVPN ‣ Client Export and select the newly created VPN server fromthe list. Leave everything default and Download the Viscosity type from thelist of export options under Export type.
Now on your Mac or Windows PC unpack the bundle and import the Viscosity.visc file.Double clicking it should be enough to get it imported. When asked for an applicationto open the file with search and select Viscosity.
Some sample screenshots (macOS):
Import Configuration
Connect & login
In the password field enter your TOTP token first followed by your password.
Connected
Android¶
For Android users we recommend using OpenVPN for Android (https://play.google.com/store/apps/details?id=de.blinkt.openvpn)from Arne Schwabe.
Go to VPN ‣ OpenVPN ‣ Client Export and select the newly created VPN server fromthe list. Leave everything default and Download the inline File only configuration from thelist of export options under Export type.
Import the hostname-udp-1194-android-config.ovpn file into OpenVPN for Android.Clicking the file should be enough to get it imported. When asked for an applicationto open the file with, select OpenVPN for Android.
iOS¶
For iOS users we recommend using OpenVPN Connect (https://itunes.apple.com/us/app/openvpn-connect/id590379981)from OpenVPN Technologies.
Go to VPN ‣ OpenVPN ‣ Client Export and select the newly created VPN server fromthe list. Leave everything default and Download the inline File only configuration from thelist of export options under Export type.
Import the hostname-udp-1194-ios-config.ovpn file into OpenVPN Connect.Clicking the file should be enough to get it imported. When asked for an applicationto open the file with, select OpenVPN Connect.
Step 4 - Multi Factor Authentication¶
For two factor authentication you need the factors username/password and a token.OPNsense supports another layer, namely a user certificate. This means that everyuser will be uniquely identified by the user certificate. In this case the multifactors are:
User certificate
Username/Password
Token (TOTP)
Go to VPN ‣ OpenVPN ‣ Servers and click the pencil icon next to the serverwe just created to change the 2FA to multi factor authentication.
Openssl Vpn Docker
Now change Server Mode to Remote Access (SSL/TLS + User Auth) and leaveeverything else unchanged. Click Save on the bottom of the form.
Openssl Vpn Certificate
Now when you go to the client exporter, you will see that each user is listed separately.In our case we see Donald listed. Exporting and importing this configuration worksexactly the same as before, the only difference is that each user requires a User certificateand therefore their own configuration.